Over the past thirty years or so of the modern era of IT Security, now called Cybersecurity by most, many things have changed. Networks have gotten faster, applications are deployed in a multitude of ways, and the computing model itself has changed from centralized to distributed and back a few times.
During these changes, the basic tenets of security have stayed the same. Protect your data and systems from being compromised, keep the data integrity, and make the systems available. IT practitioners have a long list of things to consider when it comes to enforcing security controls and growing an IT Security practice. One subject that tends to be overlooked, especially in new or immature IT Security practices is the use of a framework.
A security framework is a set of requirements that can be used to assess the status of the IT Security of an organization that takes into account all areas of risk including but not limited to physical security, endpoint protections, security operations, and acquisition of IT products and services. The framework allows an organization the ability to measure where they are currently, decide where the organization needs to be to address risks to the business, and then identify and ideally close the gaps that exist.
There are also many compliance requirements that an organization may be subject to including HIPAA, PCI, Sarbanes Oxley, and the NIST 800-171. These are typically focused on a market vertical, a type of data, or other narrow set of requirements. They differ from a framework because they are typically a set of pass/fail or compliant/non-compliant controls or requirements. A framework is ideally designed to allow an organization to utilize it regularly to make decisions regarding investments in IT and business decisions driven by risk. Following any of the compliance requirements listed above is certainly a step in the right direction, but an organization may leave some risk unaddressed if the focus is too narrow.
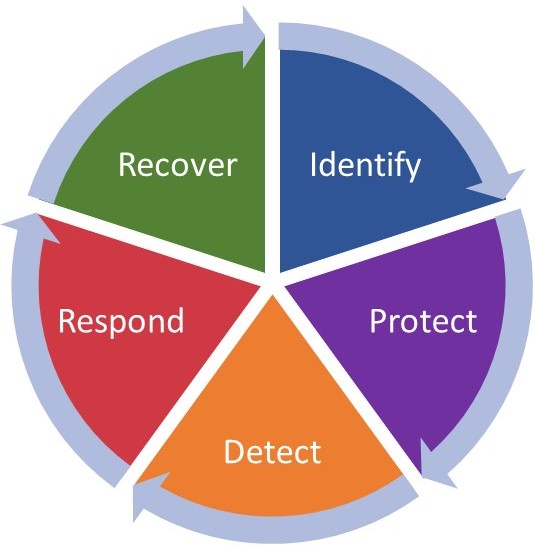
The NIST Cybersecurity Framework is growing in popularity as each day passes and is being adopted by public, private sector, and government entities. There are many reasons for this growth in adoption and they should be considered by your organization. The National Institute of Standards and Technology (NIST) has been creating IT Security guidance for decades and the content is open to anyone who wants to read it. In addition, there are many crosswalks and mappings to existing IT Security compliance requirements, like those above. You can manage the compliance of your organization within the NIST CSF while also improving the maturity of the practice as a whole.
The framework is designed to be used as a risk-based maturity model to assess the status of the organizational security practice and then make decisions regarding where you will make improvements to close gaps. It also allows for an organization to accept risk, as opposed to “failing” the requirements of compliance. An assessment using the NIST CSF is ideally conducted by a third party that has an objective view of your IT and IT Security practice.
When utilized well, the NIST CSF can act like the playbook that coordinates teams and moves the organization in the same direction. It can allow you to communicate risk to senior leadership, quantify costs and necessary budget, partner with your peers, and delegate the necessary actions to remediate vulnerability and risk.